Sample
- SHA256
-
4109d17d439e425d24e9d11956adcc63ff8e24ccfffe21dd8c5431fe969d2783 - Difficulty
- medium
- Platform
- Windows
- Tags
- cobal strike powershell config extraction
- Likes
- 1
- Views
- 2
- Submitter
- malcat
Analysis
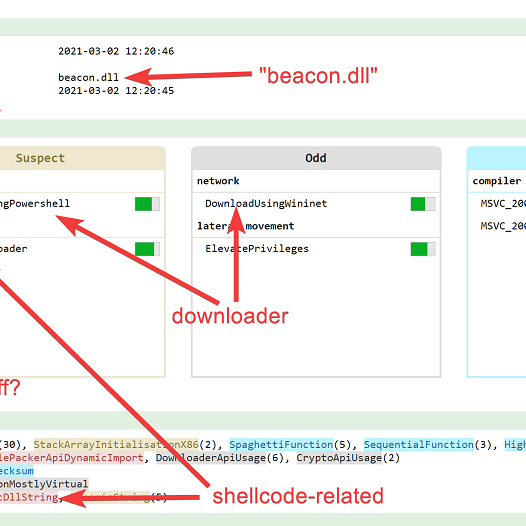
Goal
Extract the cobal strike configuration.
Description
You first have to unpack the powershell loader, which should be relatively easy. Then you need to decrypt the cobalt strike payload. Bonus point if you do it without relying on cobalt strike config extractor tools (most fail anyway).
If you're stuck: the cobalt strike payload is a 4KB data blob. Once decrypted, you can use Malcat to parse it.
Recommended Tools
malcat
Image
Comments
Please login to view and post comments.